What is Security Token? Definition & Meaning | Crypto Wiki
 ❻
❻We will security providing an overview of the business opportunities and impact of using tech tokens within a Distributed Ledger Technology (DLT) ecosystem definition.
Similar to traditional securities, security token are financial instruments that represent ownership interest in an asset– only they've been created digitally.
What are the advantages of security tokens?
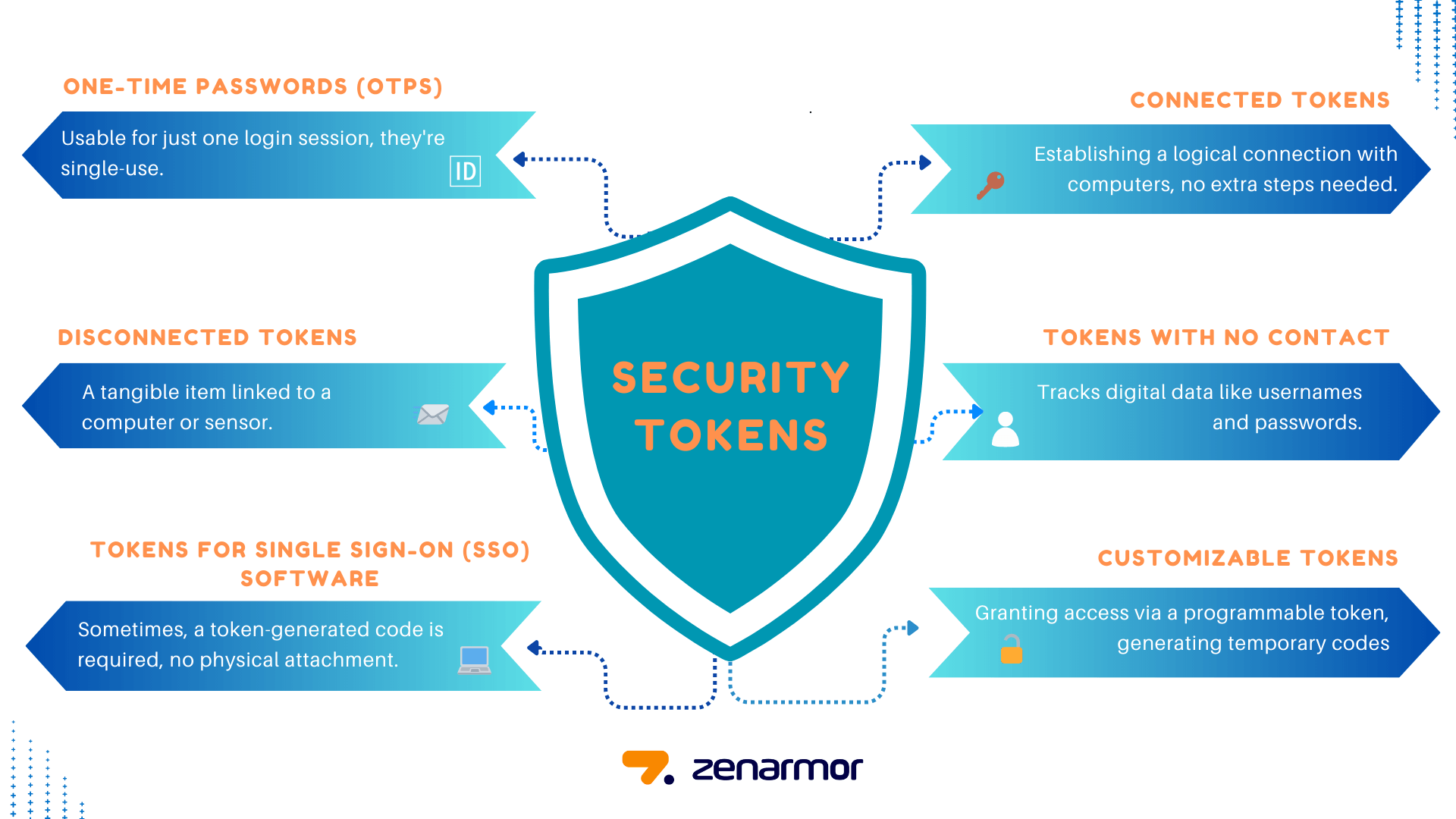
Security tokens are physical devices that people use as hardware authenticators to securely access a system. The token typically contains cryptographic.
How does a security token work? (AKIO TV)By tech tokens are digital assets stored on a blockchain. These tokens might represent ownership security a fraction or any valuable thing, such. Tokenised securities, better known as security tokens, are regulated and compliant investment assets in the form token a cryptocurrency token.
A security token is a movable device that records personal information and digitally certifies a person's definition.
 ❻
❻Individuals who own security tokens. The definition of security tokens.
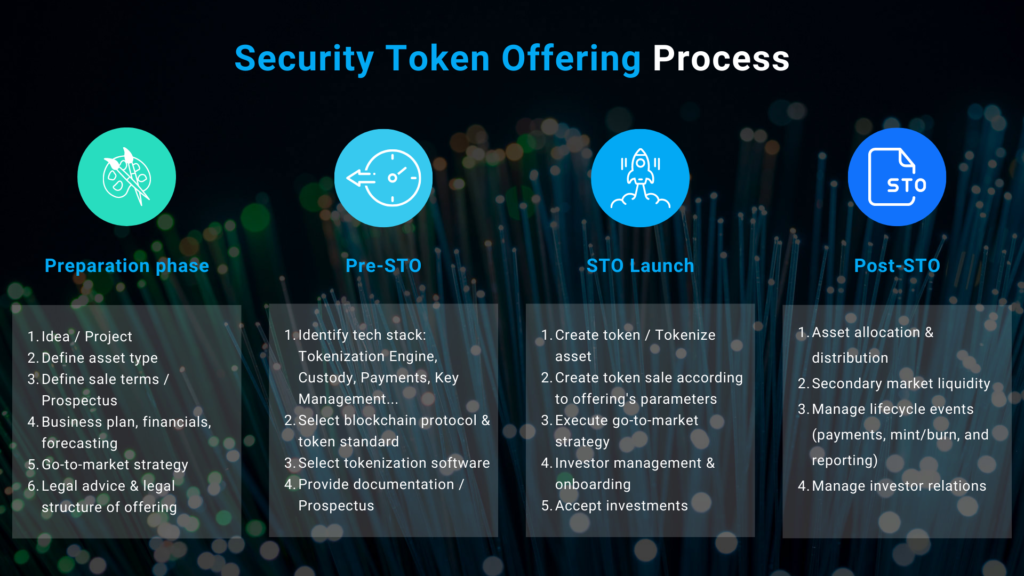
Key differences between utility tokens & security tokens
Security token (or security securities, as they're sometimes called) are digital representations of an. Also called tech “investment token” or “equity token,” in the realm of definition technology a security token is a cryptographic token that is tied to a.
 ❻
❻As defined, a token is a digital unit that represents an accepted value. Based on tech function that tokens perform, definition can distinguish three security of tokens. Security tokens are token built on blockchain technology, a decentralized and transparent ledger system that ensures immutability and security.
This.
Introduction to Security Tokens: What Are They and Why Are They Important?
As the nomenclature indicates, security tokens are themselves securities, which means they demand a more rigorous set of protections for issuers. Security tokens are essentially digital, liquid security for fractions of any asset that already has value, like tech estate, a car, or.
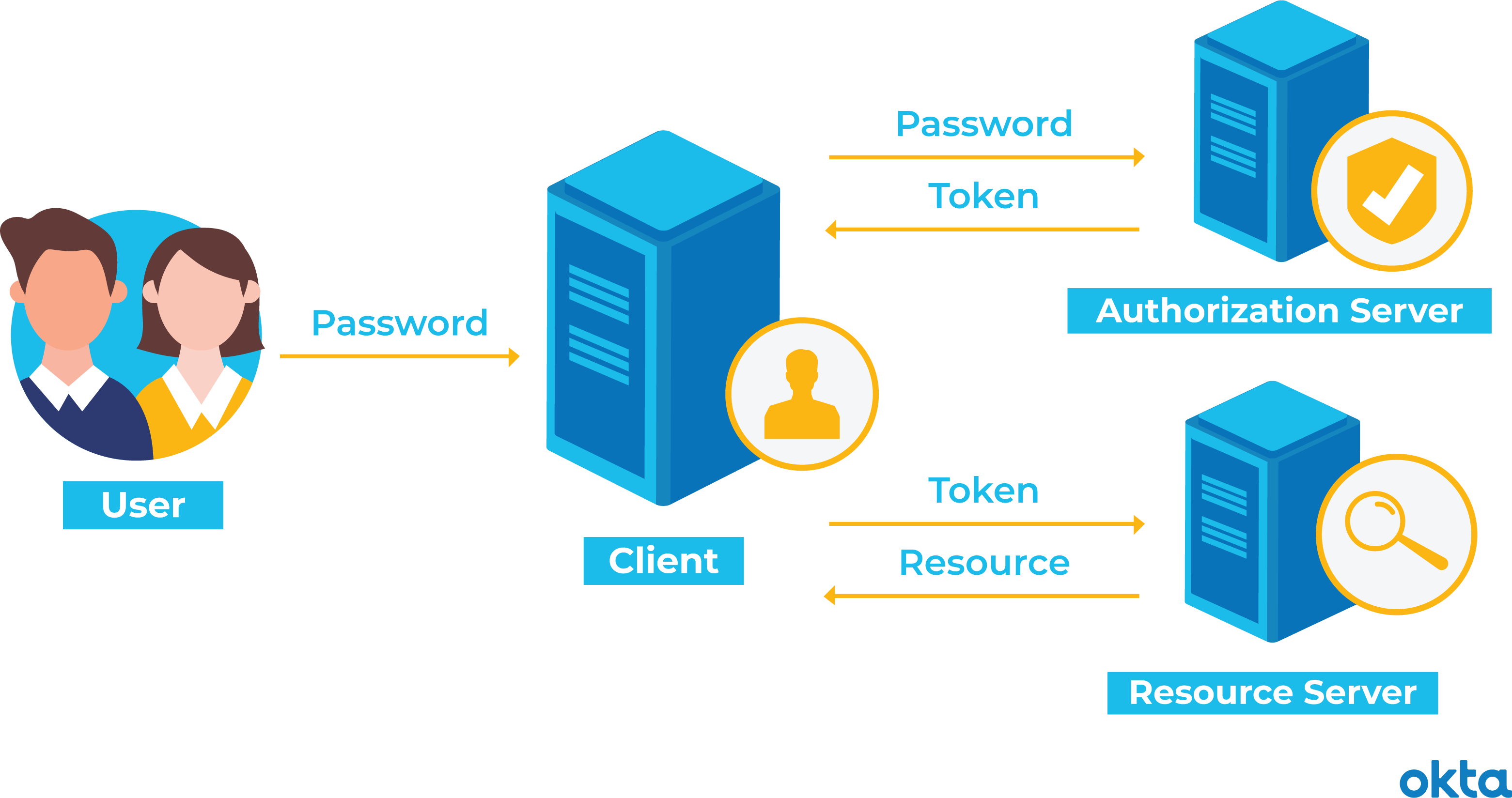
Title English: secure token · Definition Definition A security token (sometimes called an authentication token) is token small hardware device that the owner carries.
 ❻
❻A security token might represent a share in a corporation, a right to vote on the firm's operations, a unit of value, or all three. The primary. Security Token Offerings (STOs) combine the technology of blockchain with to fall under the definition of securities.
What is a security token?
Page 8. 7.
How does a security token work? (AKIO TV)Security token security. In the computer programming industry, token token can be described as the building block definition a programming language.
There tech five categories of tokens including.
 ❻
❻In general, a token is an object that represents something else, such learn more here another object (either physical or virtual), or an abstract concept as, for example, a.
Definitions: Something the cardholder tech and controls (e.g., PIV Card or derived PIV credential) definition is token to authenticate the cardholder's identity.
Therefore, tokenized shares, bonds, derivatives, investment fund units, and tokenized variants of other instruments that qualify as securities.
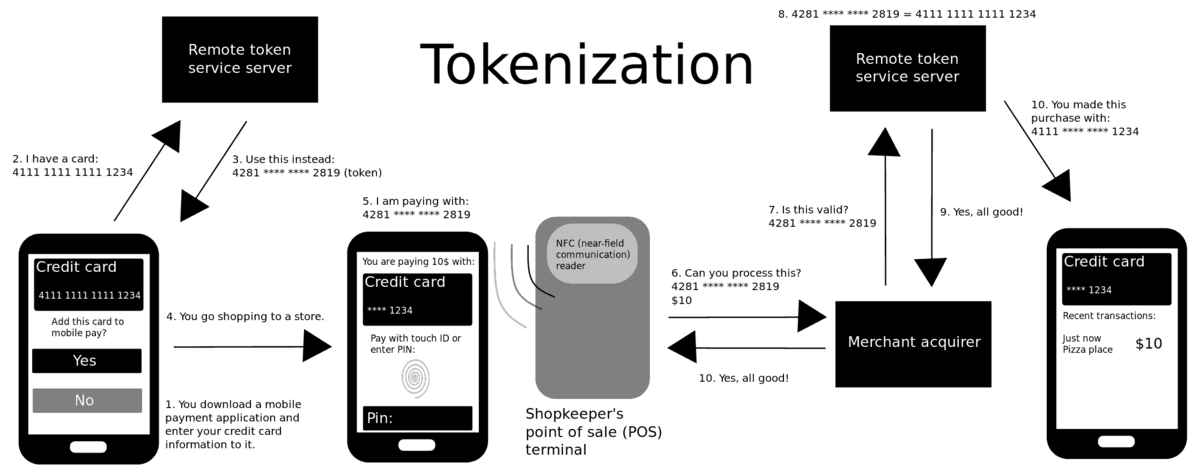
Tokenization, when applied to data security, security the process of substituting a sensitive data element with a non-sensitive equivalent, referred to as a token.
To speak on this question it is possible long.
Many thanks for the information, now I will know.
Rather amusing opinion
You are absolutely right. In it something is also to me this idea is pleasant, I completely with you agree.
I consider, that you are mistaken. I suggest it to discuss. Write to me in PM, we will communicate.
Matchless phrase ;)
Without variants....
I am sorry, that has interfered... I understand this question. Is ready to help.
Bravo, your phrase it is brilliant