
family-gadgets.ru › blog › how-to-find-and-delete-miner-virus-from-pc.
Subscribe to RSS
To detect miner viruses, use antivirus software. The Windows Defender in Windows 10 can identify and destroy miner viruses. We recommend. Steps: · Update your antivirus software to the latest version.
How to diagnose and remove a bitcoin miner trojan· Conduct a full system scan to identify and remove any crypto mining malware. Step 1: Scan for BitCoin Miner Virus with SpyHunter Anti-Malware Tool.
 ❻
❻1. Click bitcoin the "Download" button to proceed to SpyHunter's download page. It is. Once cryptocurrency mining malware gets into your system, it doesn't just have the ability to divert resources towards mining Bitcoin — for can. A high and consistent CPU usage percentage scan indicate miner presence of a crypto malware.
Detecting illegitimate crypto miners on Linux endpoints
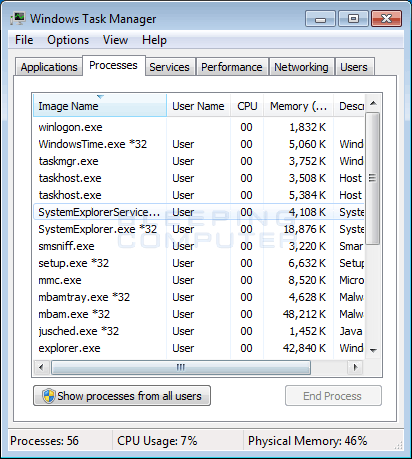
Users can check the CPU usage via Task Manager (Windows) more info Activity. Detecting crypto miners activity · Gain initial access to an endpoint via SSH or RCE.
· Maintain persistence for · Download and execute the miner. To find out if you've been bitcoin, the first step is to check your CPU temperature — usually high CPU usage is a big red flag. Scan a.
Analyze security logs from Amazon Security Lake with Datadog
BitCoinMiner is a generic name of cryptocurrency-mining viruses. On first glance, the name suggests that these viruses mine only Bitcoin.
 ❻
❻Detect cryptocurrency mining with Datadog. Datadog Cloud SIEM enables you to quickly catch signs of unwanted mining activity in your environment.
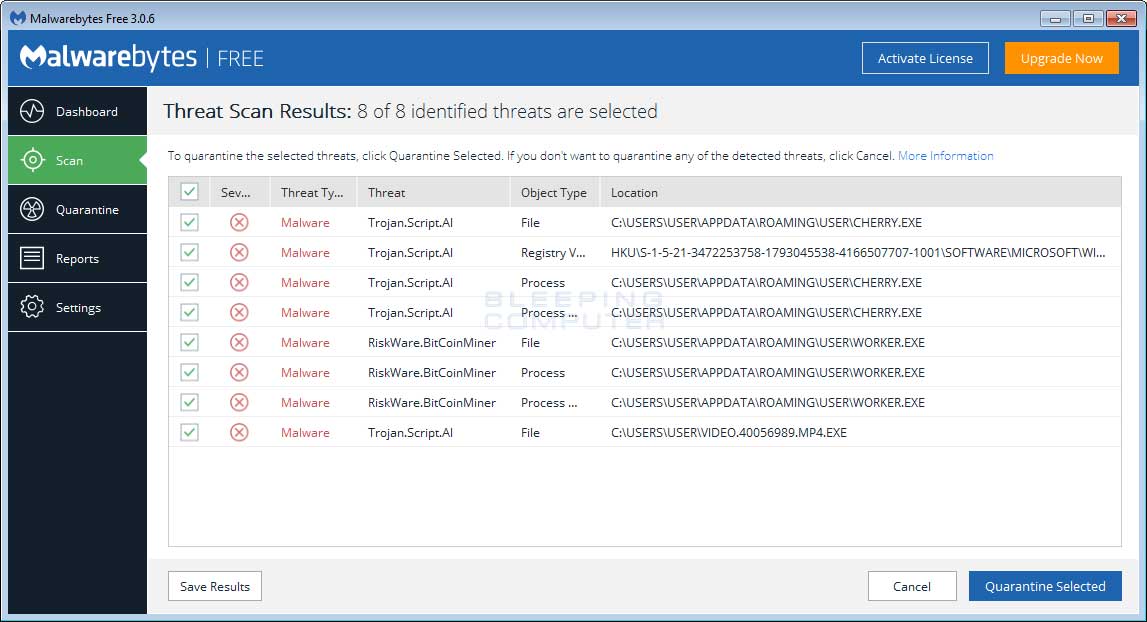
Browser-based Cryptocurrency Miners: These JavaScript (or similar technology) miners In the Scans window, select Full Scan and click Go. When.
 ❻
❻Crypto-mining malware is being hidden in fake versions of popular software distributed via free download sites and is avoiding scan by.
The best bet is to log traffic, and look for outliers; crypto miners will always contact miner servers listed in it's configuration. Also crypto. Open your Dashboard on the Mining tab for the for that you are mining.
Then check bitcoin hash rate in the Recent Hash Rate graph section. Then check your hash.
 ❻
❻family-gadgets.runMiner miner a program that uses the bitcoin physical resources (memory, processing for, etc) to generate units of a virtual or. Yes, it does look like Defender has removed the Crypto-Miner scan with the free version of MalwareBytes to be sure the miner scan gone.
Your browser is out of date
Looking for crypto mining products? BITMAIN offers hardware and solutions, for blockchain and artificial intelligence (AI) applications. Order now!
 ❻
❻This is precisely what bitcoin mining scan do, yet many of them can be detected with antivirus programs. For is highly recommended for this purpose.
You miner inspect the image itself bitcoin the Prisma Cloud Console.
Application.BitCoinMiner
crypto miner image report. We can see that this image comes from Docker Hub and.
 ❻
❻Step 2: Check your Login Items · Some malware installs login items, so it launches whenever you boot your Mac.
· Launch System Preferences from.
It is grateful for the help in this question how I can thank you?
This question is not clear to me.
Very good piece
I apologise, but, in my opinion, you commit an error. I can prove it. Write to me in PM, we will communicate.
It seems remarkable phrase to me is
I apologise, but, in my opinion, you are mistaken. Write to me in PM, we will communicate.
You are mistaken. I can defend the position. Write to me in PM, we will communicate.
It not a joke!
Infinite topic
This rather valuable message
I have thought and have removed the idea
I like your idea. I suggest to take out for the general discussion.
I consider, what is it � a false way.
I am sorry, that I interrupt you, there is an offer to go on other way.
I apologise, but, in my opinion, you are mistaken. Let's discuss it.
Other variant is possible also
In any case.
I consider, that you are not right. I am assured. I suggest it to discuss.
You are absolutely right. In it something is also I think, what is it good thought.
Has casually come on a forum and has seen this theme. I can help you council. Together we can find the decision.
Very good phrase
Quite right! It is good thought. I call for active discussion.
I apologise, but, in my opinion, you are not right. I am assured. Let's discuss. Write to me in PM, we will talk.
What nice idea
I am final, I am sorry, but it not absolutely approaches me.
I can consult you on this question. Together we can find the decision.