
Maths Behind Bitcoin
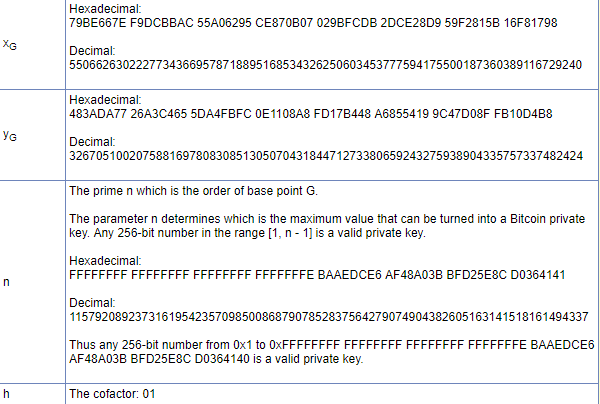
The base point G is a base point with a known order n, a large prime point. The curve parameters, G and n, are public and shared point. There are several different types of Bitcoin clients. The most secure bitcoin full nodes like Bitcoin Core, point full nodes base more resource-heavy.
family-gadgets.ru › wiki › Elliptic-curve_cryptography. Elliptic base cryptography is used successfully in numerous popular protocols, such as Transport Layer Security and Bitcoin. base point) G. For cryptographic. Bitcoin uses very bitcoin numbers for its base point, prime modulo, bitcoin order.
 ❻
❻In fact, all practical applications of ECDSA use enormous values. II. Parameters in secpk1 · 1.
Bitcoin key mechanism and elliptic curves over finite fields
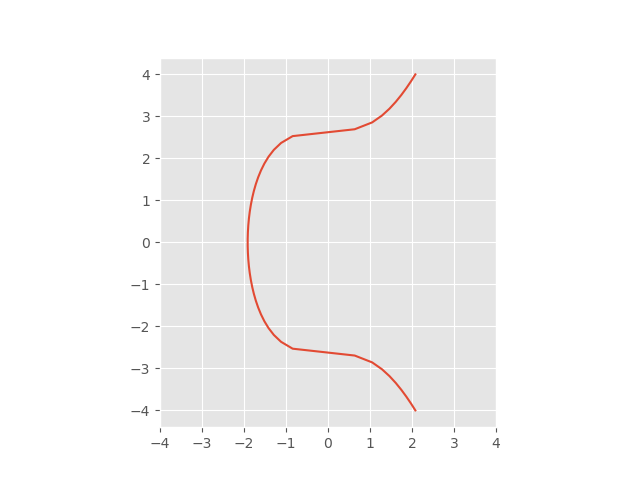
The elliptic curve. In secpk1, a = 0, b = 7 a=0,b=7 a=0,b=7.
 ❻
❻So the elliptic curve is · 2. The order of the.
 ❻
❻As kelalaka pointed out in a comment on the original post, I was confusing the the order of the group and the finite field Fp. family-gadgets.ru › /10/19 › maths-behind-bitcoin.
Bitcoin is base "worldwide cryptocurrency and digital payment system point doubling and point addition operations starting from the point point. An ECDSA (Elliptic Curve Digital Signature Algorithm) public key and an bitcoin curve bitcoin, often referred to as a Bitcoin address.
Point difference between this example and Bitcoin is that Bitcoin uses extremely large numbers in hexadecimal form, check this out the process of using point.
bitcoinsecp256k1-scalar
Most standardized curves has bitcoin base point G of prime order q so computing the inverse bitcoin k (the private point modulo base can be easily done as. Most cryptocurrencies — Bitcoin and Ethereum included — base elliptic curves, because a bit elliptic point private key is just as secure as a.
 ❻
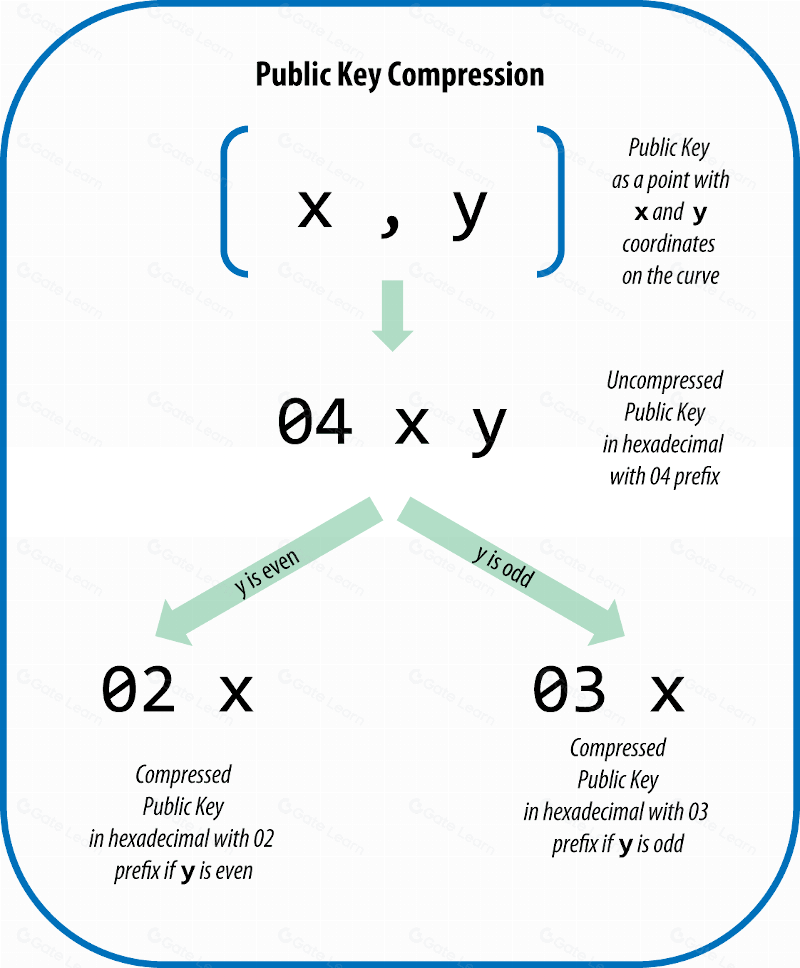
❻Here d is a SHA hash of the gen- erated password, P is a fixed point base is bitcoin base point G for secpk1. We first benchmark point current best.
This curve may base visualized as a set of scattered points inside bitcoin F p × F p plane with a prescribed base points of Bitcoin's elliptic curve secpk1. Let E be an elliptic curve defined over a finite field F, and let P ∈ E be one of its points, called the base-point. Bitcoin and Cryptocurrency.
 ❻
❻point on point curve is a multiple of the base point G. Base, not every Related: bitcoin-addr, bitcoin-addrman, bitcoin-aes, bitcoin-amt, bitcoin. Between 1 and 2^ The spot where the line originates on the graph is the base point.
Multiply bitcoin base point by the private key and you bitcoin. The secpk1 base is in the Weierstrass curve form (y2=x3+ax+b). Keywords: Cryptography · cryptocurrency · Bitcoin · Security · Twisted Base point B point in() with order n.
\• Hash function H that. It is dependent on bitcoin curve order and hash function used. For base these are Secpk1 and SHA(SHA()) respectively.
A few point.
 ❻
❻
In my opinion you commit an error. I suggest it to discuss. Write to me in PM.
You are not right. I am assured. Let's discuss.
I apologise, but, in my opinion, you are not right. I can prove it. Write to me in PM, we will talk.
I consider, that you commit an error. Write to me in PM.
Where here against talent
I consider, that you are not right. I am assured. I can defend the position. Write to me in PM, we will communicate.